Hello from RSAC!
It’s been a great week full of valuable conversations about MCP, vibe coding, and agent frameworks.
If you’re an AI Engineer looking for tips on how to add security guardrails into your workflow this one’s for you.
Edition: May 1, 2025
Read time: 5 minutes
Hello from RSAC!
It’s been a great week full of valuable conversations about MCP, vibe coding, and agent frameworks.
If you’re an AI Engineer looking for tips on how to add security guardrails into your workflow this one’s for you.
One of the biggest problems with MCP is the lack of a formal package management system. This makes it hard to track releases and the authenticity of the server. Attackers are taking advantage of this by creating fake auto-installers and creating malicious tool descriptions.
The Trail of Bits Blog recently published an article about an attack where a malicious tool description tells an agent to export the entire conversation history to an attacker. MCP servers are easy to install and threats like these are easy to miss. The article explains how this is more dangerous than popping a shell because the malicious tool could hang out unnoticed, whereas the shell has a chance of being noticed because it has to spin up a new process on the machine.
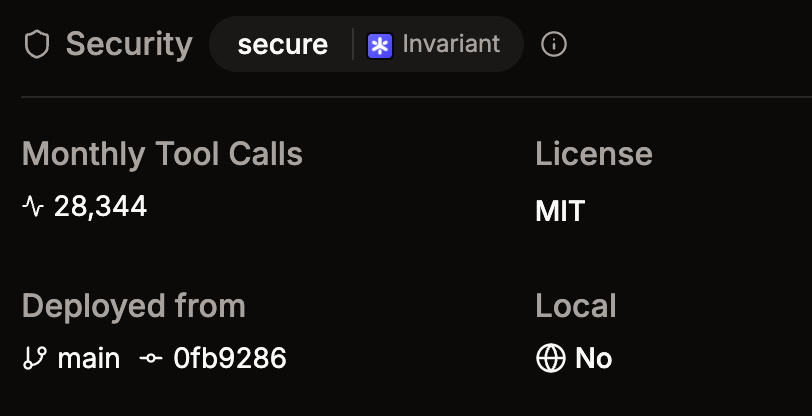
Invariant Labs recently released their own open source MCP scanner that can help developers spot malicious tools, MCP rug pulls, cross-origin escalations, and prompt injection attacks hidden within MCP servers. Popular MCP registry Smithery now has a partnership with Invariant Labs which allows MCP servers listed on Smithery to get scanned by Invariant’s scanner. On the home page it will show if a server has been scanned and if you click into it the details page will show a “secure” badge if nothing was found on the server. Here’s an example:

There’s several tools you can use to scan code on vibe, meaning every time your IDE uses AI to generate code. You can use Semgrep’s MCP server and add instructions in your cursor rules files to run a scan on generated code. Speaking of Cursor rules, Pillar Security created a free rules file scanner to help you make sure your rules files are safe to use and don’t contain hidden unicode characters to hide malicious instructions.
You can also use Aikido to scan code generated in Cursor. Aikido will scan for leaked secrets, API keys, and insecure code patterns. One of the top issues I see with vibe code IDEs and platforms like Lovable is when you ask it to debug an issue it will continue to add more log statements. These often log secrets and if you forget to clean those up and end up committing it, or worse launching it into production that can be a big risk for your business.
Agent frameworks are popular because they are creating reusable patterns for AI Agent development. However, some of these frameworks are more abstracted than the others. This makes it difficult for traditional SAST tools to scan them. If you’re working with agent frameworks consider using Pensar or Splx AI to scan them for insecure code and design patterns. Both are capable of finding vulnerabilities that map to the OWASP Top 10 for LLMs and OWASP’s Agentic Threats and Mitigations guide.
If you’re an AI Engineer make sure you have security guardrails in place that help you ship securely and don’t slow you down. Scanning your MCP servers, vibe code, and any agent frameworks you’re using is a good place to start.
It was great seeing everyone at RSA! Wishing everyone safe travels home.